Rod Kinghorn, David Dryfus and Justin Heinonen, 2013
Supply chain management can be the first step for preventing product counterfeiting. This Backgrounder addresses how stakeholders in a supply chain can mitigate and prevent this crime by moving towards a more comprehensive purchasing strategy.
A typical supply chain is comprised of a network of a brand owner directly involved in the flow of products, services, finances and/or information (see Figure 1). A supply chain is defined as a “network of organizations and activities involved in designing, transforming, consuming and disposing of goods and services.” We all participate in supply chains every day by buying and consuming goods and services, but many of us may not consider how products are created and end up in our hands.
Figure 1: Typical Supply Chain
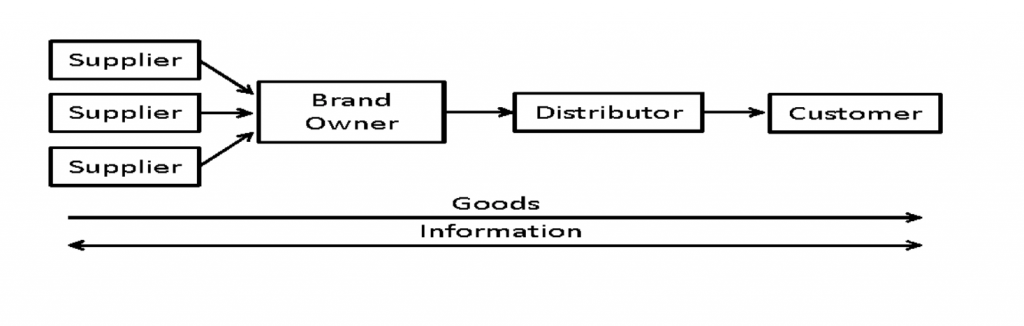
Figure 2: Brand Owner’s Electronic Goods Supply Chain
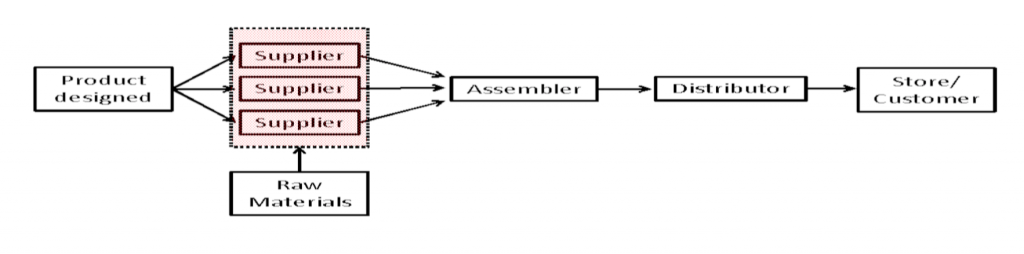
As an example, let’s suppose Figure 2 represents a brand owner’s electronic goods supply chain. The product is designed in the United States, where intellectual property rights are strongly defended. These designs contain the instructions to make the brand owner’s product and are sent to its suppliers throughout the world. The suppliers use the designs to buy the appropriate amounts of raw materials and then transform these materials into components needed to make the product. The components then are sent to an assembler who puts them together in the right order to make the final product. Finally, the finished product is shipped to customers and retailers around the world. By the time the product reaches the consumer, the contents may have traveled across the ocean and been handled by dozens of people. Most supply chains are similarly complex and at-risk for potential disruptions from product counterfeiting and more.
In the course of conducting business in a global economy and because of supply chain risks, prudent brad owners have a purchasing strategy to select suppliers. Traditionally, this strategy uses cost and quality as a way to evaluate and select suppliers. However, a more comprehensive purchasing strategy may be needed to account for the potential costs of risk management. A purchasing strategy may be thought of as a systematic method in which one chooses suppliers and other partners with which to work. Risks exist throughout a supply chain that may cause disruptions to production and jeopardize the ability of a brand owner to deliver safe, authentic products, on schedule. Some of these risks include substitution of counterfeit products, contamination of materials, delays of transportation of goods, recalls of products, natural disasters, theft of intellectual property, and many others. While not all of these risks are preventable, such as natural disasters and some delays, many of them are manageable if planned for in advance.
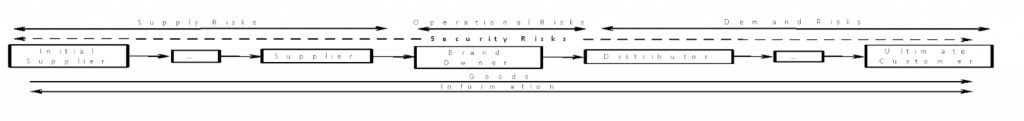
Figure 3: Supply Chain Risks
Figure 3 shows that risks for introducing counterfeit products often exist after the brand owner sells the genuine product to the distributor, and before the ultimate customer receives the product. Introduction of counterfeit products at this point in the supply chain is difficult to detect by the brand owner because the genuine product is no longer in its direct control. In addition to the low risk involved, the distributor may introduce counterfeit product at this stage to become more competitive in the market for selling to the ultimate customer. This frequently involves direct competition with the brand owner, which is only possible because of the lower cost point of the counterfeit product. Both the brand owner and the ultimate customer lose value when this occurs, as the brand owner’s sales are compromised and the ultimate customer is buying a product that is counterfeit and may not meet the quality standards of the genuine and in some cases could be a safety risk. In this example, the terms and conditions of the contract between the brand owner and the distributor are the tools needed for the band owner to detect and correct the supply chain disruption caused by the introduction of counterfeit product into the supply chain by the distributor.
Therefore, a brand owner may benefit from viewing its supply chain as a “community” consisting of a brand owner’s partners, shareholders, customers, suppliers and other stakeholders. To increase supply chain security, a community approach suggests brand owners build close ties and trust with their suppliers through sound business processes and legal agreements. This increases information sharing and a brand owner’s ability to better monitor their suppliers (and their partners), which may help them respond more effectively and promptly to supply chain disruptions, like product counterfeiting. In the following sections, we discuss how building a more robust supply chain and recognizing potential risks can mitigate and even prevent product counterfeiting.
Risk Management
Risk management is a major component of supply chain management research Product counterfeiting is one of many supply chain risks that companies face given today’s complex and global business environment. While many high-profile incidents involve food and pharmaceutical products, such as the 2008 case involving infant formula from China containing melamine, product counterfeiting threatens virtually every type of industry. Even the U.S. government has fallen victim to counterfeit products; for instance, recall the incident involving counterfeit electronic circuits ordered by NASA. To ensure a safe and secure supply chain to better protect against counterfeit products, a systematic business process should be put into place and actively managed. Below, we discuss four specific components of such a process.
Process Management
A management process that allows a brand owner to plan, detect, respond to, and recover from security incidents is critical for a safe and secure supply chain. When developing these processes it is important to have input from senior management, middle management and other office and line workers who are often included in these planning scenarios so that many different angles to the situation are evaluated. Processes should be developed that identify the difference between routine and escalation action plans. Plans designed to react to counterfeit products that don’t pose a high risk to the consumer would most likely involve more of a routine process for investigation and remediation than a counterfeit product that did pose a safety risk for consumers. Such processes can be developed based on “scenario planning” which helps businesses better prepare for an actual security-related event. Scenario planning includes role-playing, where a mock situation is presented and the brand owner attempts to respond. This tactic is particularly effective at helping a brand owner become more aware of weaknesses within their supply chain,
helping them identify where counterfeit products are more
likely to enter and who are likely potential offenders. The practice scenarios help all of those participating identify the differences between high and low risk counterfeit situations, which creates a process better able to respond to the high-risk and highly stressful disruptions when they occur.
It is important to note that some sales of counterfeit products which are sold to the Ultimate customer may not be preventable by the brand owner, since they may enter through an illegitimate supply chain. Therefore, a process must be in place for detecting, reporting, and investigating potential counterfeit product sold through both the legitimate and the illegitimate supply chains.
Using the methods above facilitates early detection of counterfeit products, which likely reduces harm to a brand owner’s financials and reputation, as well as risks to its customers. The effectiveness of a brand owner’s response to counterfeit products depends largely on taking swift and proper action. In summary, by thinking ahead and planning for various scenarios, a brand owner will have a process to detect, respond to, and recover from counterfeit products entering the supply chain, thus putting it in a better position to recover from a counterfeiting incident.
Information Sharing
A major debate in developing a purchasing strategy is information sharing. Specifically, the question is how much information should be shared with suppliers and customers? The easiest answer is, “it depends.” The actual answer, however, is much more complex and multiple factors must be considered. When it comes to security-related incidents like product counterfeiting, the flow of information from trusted suppliers can provide the first line of defense. Since communication typically travels much faster than the flow of goods and materials, the flow of information is key to identifying potential disruptions within a supply chain. Also, by sharing information, mutual trust is built among members within a supply chain, which can help reduce risks of all types. Therefore, contracts are key components for establishing relationships and information sharing. It is recommended that brand owners should specify in all contracts that tier 1 suppliers are responsible for enforcing the terms and conditions of the contract with any tier 2 or tier 3 suppliers used by the tier 1 supplier to fulfill the contract with the brand owner.
Partner Security Management
Research shows that integration among brand owners, suppliers and customers helps companies respond to supply chain disruptions. Partner security management, for instance, heightens the idea of sharing information between companies and their suppliers and other supply chain partners. Specifically, it involves further collaboration to increase mutual trust between a brand owner and its suppliers. Again, the terms and conditions of the contract are key to identifying expected behaviors that suppliers follow. The ability to follow these rules can be monitored and used as a way to evaluate their trustworthiness and reliability. Additionally, supplier certification and audit programs can further ensure their compliance with proper supply chain procedures.
Service Provider Security Management
Service provider security management has the same purpose as partner security management, but is focused on service providers. Specifically, brand owners should screen and audit service providers and train their own personnel to be aware of risks that could result in contamination of their products. For example, when transportation carriers are hired, the procedures for hiring their drivers and monitoring their vehicles while goods are transported may not be fully developed. Maintaining the integrity of cargo during transportation is a key element when monitoring the performance of a carrier. Contracts should specify how the transportation carrier will accomplish this and the brand owner should expect to audit or monitor the performance of the carrier to ensure compliance. Special care should be given to the movement of materials that could be easily converted to counterfeit if stolen or misrouted during this process. Examples would include excess and obsolete product being moved without packing, scrap materials, “stock lifts” and material returns.
The First Steps toward Establishing a More Secure Supply Chain
Armed with the information above, what can brand owners do now to better detect and reduce the number of counterfeit products in the supply chain? First, be an advocate of supply chain security at your company and help senior management understand the specific risks. After gaining their support, it is important to develop a product quality assurance process plan to implement measures to maximize the availability of authentic, originally designed, and qualified parts, thus increasing your supply chain security. Your plan should involve training those who interact with your suppliers, customers, and the product or service your company offers on what to do if counterfeit products are suspected. Recognize that most counterfeit product is difficult to positively identify without significant analysis. However, successful brand owners should have a policy that clearly identifies the process for reporting, investigating and taking appropriate actions to protect the integrity of their brand. These actions could include contractual, civil or criminal actions including prosecution by local, state, federal or international law enforcement.
Next, equip your suppliers with the same knowledge as your employees regarding the reporting of suspected counterfeit products. Furthermore, assessing your suppliers’ risk of counterfeit products entering their markets will help you determine how to best manage your time and employees. Those suppliers with lower risks will not need as much monitoring as those with higher risks.
If you are in the business of selling finished products made by other brand owners, you can mitigate the risks of procuring counterfeits by avoiding “spot buying,” in which someone tries to take advantage of a time-sensitive opportunity to purchase components or materials at a lower cost, often from an unfamiliar supplier. You could control with whom your purchasing agents interact by providing them a list of preferred suppliers and distributors who have demonstrated successful counterfeit avoidance procurement processes.
Additional Measures to Consider
While the previous section stresses the importance of processes and knowledge sharing as some of the first steps to take to establish a more secure supply chain, technology can help as well. Government agencies and brand owners have implemented more technical solutions to “track and trace” genuine products moving through their supply chains. This can be critical, since counterfeiters are becoming more sophisticated with marketing products that look identical to the genuine. Some brand owners use DNA marking for parts, which improves traceability, assists in the management of any recalls, and ensures that the parts have come from the correct supplier. Another solution is using radio frequency identification devices (RFIDs), which allows brand owner to monitor the location of their products in the supply chain. While not without significant
cost, the increased ability to track your components and products throughout the supply chain is being welcomed by many, especially customers. Perhaps spurred by recent headlines about food recalls, counterfeit pharmaceuticals and the like, consumers increasingly want to know from where the products they use come.
Some brand owners have developed packaging solutions to enhance supply chain security, such as tamper-proof seals and locks. These measures ensure that products are not compromised when transported between suppliers and customers. Most consumers are familiar with tamper-proofed medicines, for instance, but many products, from clothes to electronics, receive unique locks that require special devices to remove. Both locks and seals could be used well before the item is stocked on a shelf or rack, so that the product is protected throughout the supply chain. However, the existence of these tamper-proof devices does not guarantee that the product is genuine or that all products in the marketplace are genuine. It only provides some assurance that the product has not been tampered with regardless of whether it is counterfeit or genuine.
Summary
The growing complexity of supply chains, along with incentives to continually develop new products and reduce business costs, has created product safety and security challenges. With these challenges, however, comes the opportunity to manage product counterfeiting by implementing various controls within the business model. Proactively managing the counterfeit problem with a total business solution strategy may be one of the most effective ways to identify suspected counterfeit product in the market place and help brand owners keep counterfeit products from entering the legitimate supply chain.
2013 Copyright Michigan State University Board of Trustees.